ThreatMiner Maltego Transforms v1.0
Special thanks to Bob McArdle (@bobmcardle) for writing all the transforms!
Maltego has long been a favoured tool of threat intelligence analysts and researchers for searching, linking and pivoting on data - and we wanted to open up ThreatMiners data in the same way. Installing the ThreatMiner transforms could not be easier, you can simply install them directly from the Maltego Transform Hub.
Just in case, here's the transform seed: http://cetas.paterva.com/TDS/runner/showseed/ThreatMiner
Rather than providing detailed descriptions of every transform, we've included a full list below of which ones we have added - all of which should be very self explanatory to existing users of ThreatMiner. Also in the Detail View for each transform result you will find a link to the same data viewable via your browser on the ThreatMiner site:
- [Threat Miner] APTNotes to Domains
- [Threat Miner] APTNotes to Emails
- [Threat Miner] APTNotes to IP
- [Threat Miner] APTNotes to Samples
- [Threat Miner] AV Detection to APTNotes
- [Threat Miner] AV Detection to Samples
- [Threat Miner] DNSName to APTNotes
- [Threat Miner] DNSName to IP (pDNS)
- [Threat Miner] DNSName to Samples
- [Threat Miner] DNSName to URI
- [Threat Miner] DNSName to Whois Details
- [Threat Miner] Domain to APTNotes
- [Threat Miner] Domain to DNSNames (pDNS)
- [Threat Miner] Domain to IP (pDNS)
- [Threat Miner] Domain to Samples
- [Threat Miner] Domain to URI
- [Threat Miner] Domain to Whois Details
- [Threat Miner] Email to APTNotes
- [Threat Miner] Email to Domains (Reverse Whois)
- [Threat Miner] IP to APTNotes
- [Threat Miner] IP to Domain (pDNS)
- [Threat Miner] IP to Organisation
- [Threat Miner] IP to SSL Certificate
- [Threat Miner] IP to Samples
- [Threat Miner] IP to URI
- [Threat Miner] IP to Whois Details
- [Threat Miner] Malware to APTNotes
- [Threat Miner] Malware to AV Companies (Detected)
- [Threat Miner] Malware to AV Detections
- [Threat Miner] Malware to Domains
- [Threat Miner] Malware to Filename
- [Threat Miner] Malware to Hosts
- [Threat Miner] Malware to Imphash
- [Threat Miner] Malware to Mutex
- [Threat Miner] Malware to Other Hashes
- [Threat Miner] Malware to Registry Values
- [Threat Miner] Malware to URL
- [Threat Miner] SSL Cert to APTNotes
- [Threat Miner] SSL Cert to IP
The transforms are all designed to make the ThreatMiner data as easy to pivot through as possible, but we also wanted them to integrate seemlessly with other popular free and paid transforms you may be using. With that in mind, a short note on entities used.
We have made a point of including no dedicated custom entities in here, but rather reusing entities others have created (with their permission) so you can also easily then move from ThreatMiner data to others seemlessly. There is no need to install anything for these
-
From the Virustotal Local Transforms of Steven Weinstein (https://github.com/Lookingglass/Maltego)
- virusTotal.IOC (for ImpHash & Mutex)
- virusTotal.AVCompany
- virusTotal.Threat (for AV Detections)
-
From Malformity Labs by Keith Gilbert (http://www.malformitylabs.com/)
- malformity.Filename
- malformity.RegistryValue
-
From Passivetotal bu Brandon Dixon and Steve Ginty (https://www.passivetotal.org/)
- pt.SSLCertificate
A big thanks to Steven, Keith, Brandon and Steve for permission to use those.
Highly Polished and Produced Video Demo
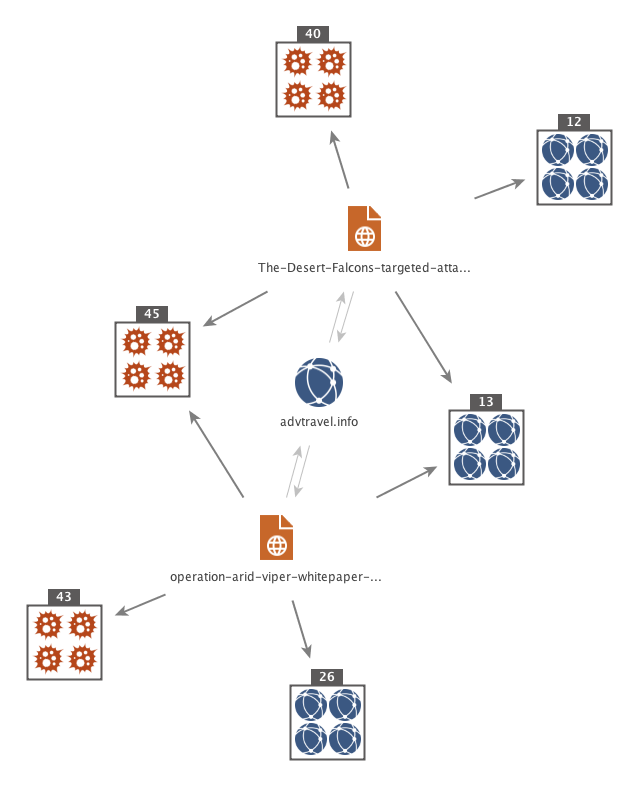
At this point in things related to Maltego you would now watch a very impressive and stylish video showing all the transforms at work. Sadly we don't have a fraction of the skill of Roelof, so here is a screenShot and an example use case instead :)
Use case:
- You notice some odd traffic on your network going to Advtravel[.]info.
- Using "[Threat Miner] Domain to APTNotes" you quickly determine that this has been reported in two seperate reports - one from Trend Micro (Arid Viper) and one from Kaspersky (Desert Falcons)
- You quickly take both reports and map them out to Domains and Hashs ("[Threat Miner] APTNotes to Domain / Samples") and from there continue to pivot out to determine further infrastructure related to the group
- from ThreatMiner data, other public sources, and your own internal sources.
Contact us
As normal, while care was taken not to have bugs in our code and the transforms where heavily tested ... there almost certainly is bugs we have not found (its code after all). For any bugs found, or feature requests please email at threatminermaltegotransforms [at] gmail.com.
User comments about ThreatMiner Maltego transforms.
